Problem
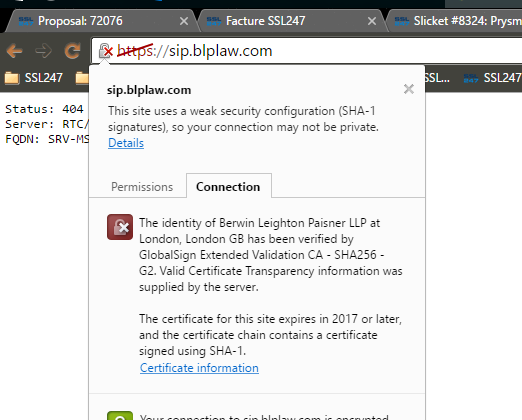
Your ESSL certificate has a double SHA-1 root, the green bar do not display on your browser:
Introduction
With the accelerated deprecation of SHA-1, it is important that the end-entity certificate (your certificate) and any intermediate certificates in the certificate chain use the SHA-256 hash algorithm. Doing so will prevent end users from receiving a downgraded user experience when connecting to your site. When you order a certificate from SSL247®, by default it is signed with SHA-256 and chains to an intermediate that is also signed with SHA-256.
Extended SSL Certificates (SHA-1 & SHA-2) chain back to CA's Root-R2 certificate. Some ExtendedSSL customers make use of a cross certificate that allows the ExtendedSSL Certificate to chain back to Root-R1 instead. The advantage at the time was that Root-R1 had greater ubiquity and extended the compatibility of the ExtendedSSL certificates. Root-R2 is now present in all major operating systems and devices and use of the cross certificate should no longer be a concern. The cross certificate counts as an intermediate certificate in the chain; since the cross certificate is a SHA-1 certificate, its usage may cause a downgraded user experience in Google Chrome and/or Mozilla Firefox even if you're using a SHA-256 ExtendedSSL certificate.
Browsers prefer chain building based on what is sent by the server, so when a SHA-1 intermediate / cross certificate is sent, the browser will prefer that over other, even shorter chains. That’s why it’s important to configure your server to send down the correct (and minimum number) of intermediate or CA Cross certificates.
Solution
See below the corresponding instructions for removing the EV Cross Certificate.
Microsoft IIS
To disable the cross certificate in IIS, it needs to be removed from the MMC.- Click Start > Run. Type MMC and press Enter.
- Go to File > Add/Remove Snap-In
- Choose Certificates and click Add
- Choose Computer Account followed by Local Computer
- Click Finish followed by OK to return to the main MMC screen.
- Click [+] next to Certificates - Local Computer > Intermediate Certification Authorities > Certificates
- Sort the list by Issued To and scroll down to your certificates.
- Find the certificate Issued To: "GlobalSign" expiring on 1/28/2028
- Right Click the entry and click Delete
- Click Yes to confirm deletion of the Intermediate certificate
- Close out the MMC. You do not have to save changes to the console settings.
- Restart IIS so that your cert now chains to Root-R2
Apache
To disable the cross certificate in Apache, it needs to be removed from your SSL configuration file.- In your httpd.conf or ssl.conf file, check the files referenced by SSLCACertificateFile, SSLCertificateChainFile, and SSLCertificateFile..
- The certificate you are looking to remove is:
-----BEGIN CERTIFICATE----- MIIETDCCAzSgAwIBAgILBAAAAAABL07hSVIwDQYJKoZIhvcNAQEFBQAwVzELMAkG A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw0wNjEyMTUwODAw MDBaFw0yODAxMjgxMjAwMDBaMEwxIDAeBgNVBAsTF0dsb2JhbFNpZ24gUm9vdCBD QSAtIFIyMRMwEQYDVQQKEwpHbG9iYWxTaWduMRMwEQYDVQQDEwpHbG9iYWxTaWdu MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAps8kDr4ubyiZRULEqz4h VJsL03+EcPoSs8u/h1/Gf4bTsjBc1v2t8Xvc5fhglgmSEPXQU977e35ziKxSiHtK pspJpl6op4xaEbx6guu+jOmzrJYlB5dKmSoHL7Qed7+KD7UCfBuWuMW5Oiy81hK5 61l94tAGhl9eSWq1OV6INOy8eAwImIRsqM1LtKB9DHlN8LgtyyHK1WxbfeGgKYSh +dOUScskYpEgvN0L1dnM+eonCitzkcadG6zIy+jgoPQvkItN+7A2G/YZeoXgbfJh E4hcn+CTClGXilrOr6vV96oJqmC93Nlf33KpYBNeAAHJSvo/pOoHAyECjoLKA8Kb jwIDAQABo4IBIjCCAR4wDgYDVR0PAQH/BAQDAgEGMA8GA1UdEwEB/wQFMAMBAf8w HQYDVR0OBBYEFJviB1dnHB7AagbeWbSaLd/cGYYuMEcGA1UdIARAMD4wPAYEVR0g ADA0MDIGCCsGAQUFBwIBFiZodHRwczovL3d3dy5nbG9iYWxzaWduLmNvbS9yZXBv c2l0b3J5LzAzBgNVHR8ELDAqMCigJqAkhiJodHRwOi8vY3JsLmdsb2JhbHNpZ24u bmV0L3Jvb3QuY3JsMD0GCCsGAQUFBwEBBDEwLzAtBggrBgEFBQcwAYYhaHR0cDov L29jc3AuZ2xvYmFsc2lnbi5jb20vcm9vdHIxMB8GA1UdIwQYMBaAFGB7ZhpFDZfK iVAvfQTNNKj//P1LMA0GCSqGSIb3DQEBBQUAA4IBAQCZIivuijLTDAd+3RsgK1Bq lpEG2r5u13KWrVM/fvWPQufQ62SlZfLz4z0/WzEMfHmEOpeMDx+uwbzy67ig70H9 vDGp/MlC5kS+HlbKdYuySTGZ/urpcWSGeo/l1WERQ+hAuzEM4tsYi5l0OGGrJICM +ag710nWZooYc8y8BjmLEDIODdOx9+9mExBZSMjPAcqZzJBymNs67cunu+JscI6m nmhj7Y+3LQWJztlU9k6rHkbbMEk/9mrgAfC8zYTUOfdVjgMVcdOdNO2dxtHIqsWE OTsN/SknUh6Dq0gjhVhQs5XGC7Mm4xYtqDDcA1BtXNEMzSqhR5rPIBvbQ4gfwvzg -----END CERTIFICATE-----
- Once you have located and removed the EV Cross Certificate, restart Apache:
sudo service httpd restart(Replace httpd with apache2 on Debian/Ubuntu based systems)
NGINX
To disable the cross certificate in NGINX, it needs to be removed from your Server Block configuration file.- Find the entry for ssl_certificate and open the referenced file in a text editor
- Remove the following certificate from the chain:
-----BEGIN CERTIFICATE----- MIIETDCCAzSgAwIBAgILBAAAAAABL07hSVIwDQYJKoZIhvcNAQEFBQAwVzELMAkG A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw0wNjEyMTUwODAw MDBaFw0yODAxMjgxMjAwMDBaMEwxIDAeBgNVBAsTF0dsb2JhbFNpZ24gUm9vdCBD QSAtIFIyMRMwEQYDVQQKEwpHbG9iYWxTaWduMRMwEQYDVQQDEwpHbG9iYWxTaWdu MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAps8kDr4ubyiZRULEqz4h VJsL03+EcPoSs8u/h1/Gf4bTsjBc1v2t8Xvc5fhglgmSEPXQU977e35ziKxSiHtK pspJpl6op4xaEbx6guu+jOmzrJYlB5dKmSoHL7Qed7+KD7UCfBuWuMW5Oiy81hK5 61l94tAGhl9eSWq1OV6INOy8eAwImIRsqM1LtKB9DHlN8LgtyyHK1WxbfeGgKYSh +dOUScskYpEgvN0L1dnM+eonCitzkcadG6zIy+jgoPQvkItN+7A2G/YZeoXgbfJh E4hcn+CTClGXilrOr6vV96oJqmC93Nlf33KpYBNeAAHJSvo/pOoHAyECjoLKA8Kb jwIDAQABo4IBIjCCAR4wDgYDVR0PAQH/BAQDAgEGMA8GA1UdEwEB/wQFMAMBAf8w HQYDVR0OBBYEFJviB1dnHB7AagbeWbSaLd/cGYYuMEcGA1UdIARAMD4wPAYEVR0g ADA0MDIGCCsGAQUFBwIBFiZodHRwczovL3d3dy5nbG9iYWxzaWduLmNvbS9yZXBv c2l0b3J5LzAzBgNVHR8ELDAqMCigJqAkhiJodHRwOi8vY3JsLmdsb2JhbHNpZ24u bmV0L3Jvb3QuY3JsMD0GCCsGAQUFBwEBBDEwLzAtBggrBgEFBQcwAYYhaHR0cDov L29jc3AuZ2xvYmFsc2lnbi5jb20vcm9vdHIxMB8GA1UdIwQYMBaAFGB7ZhpFDZfK iVAvfQTNNKj//P1LMA0GCSqGSIb3DQEBBQUAA4IBAQCZIivuijLTDAd+3RsgK1Bq lpEG2r5u13KWrVM/fvWPQufQ62SlZfLz4z0/WzEMfHmEOpeMDx+uwbzy67ig70H9 vDGp/MlC5kS+HlbKdYuySTGZ/urpcWSGeo/l1WERQ+hAuzEM4tsYi5l0OGGrJICM +ag710nWZooYc8y8BjmLEDIODdOx9+9mExBZSMjPAcqZzJBymNs67cunu+JscI6m nmhj7Y+3LQWJztlU9k6rHkbbMEk/9mrgAfC8zYTUOfdVjgMVcdOdNO2dxtHIqsWE OTsN/SknUh6Dq0gjhVhQs5XGC7Mm4xYtqDDcA1BtXNEMzSqhR5rPIBvbQ4gfwvzg -----END CERTIFICATE-----
- Restart NGINX
sudo service nginx restart
